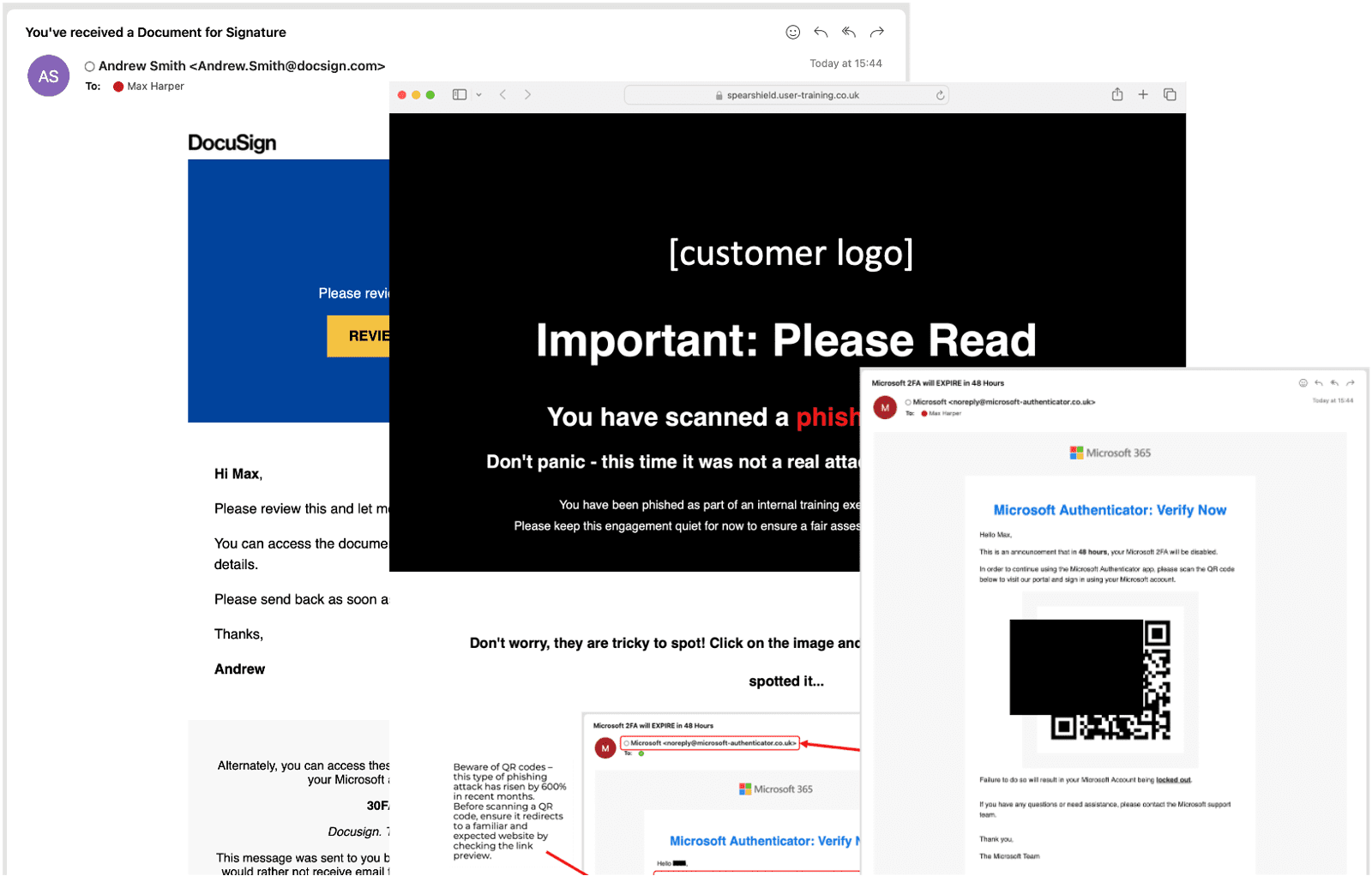
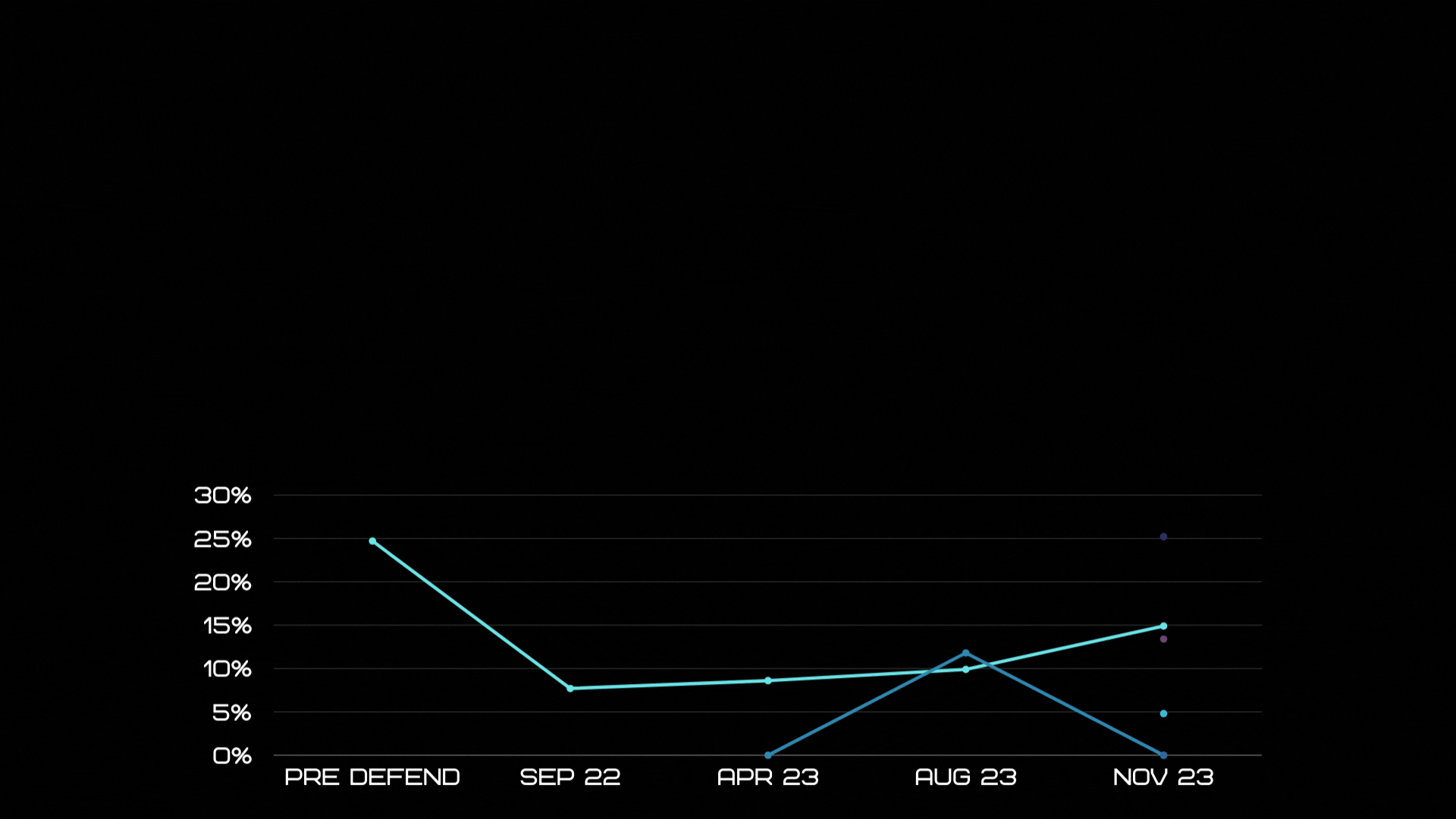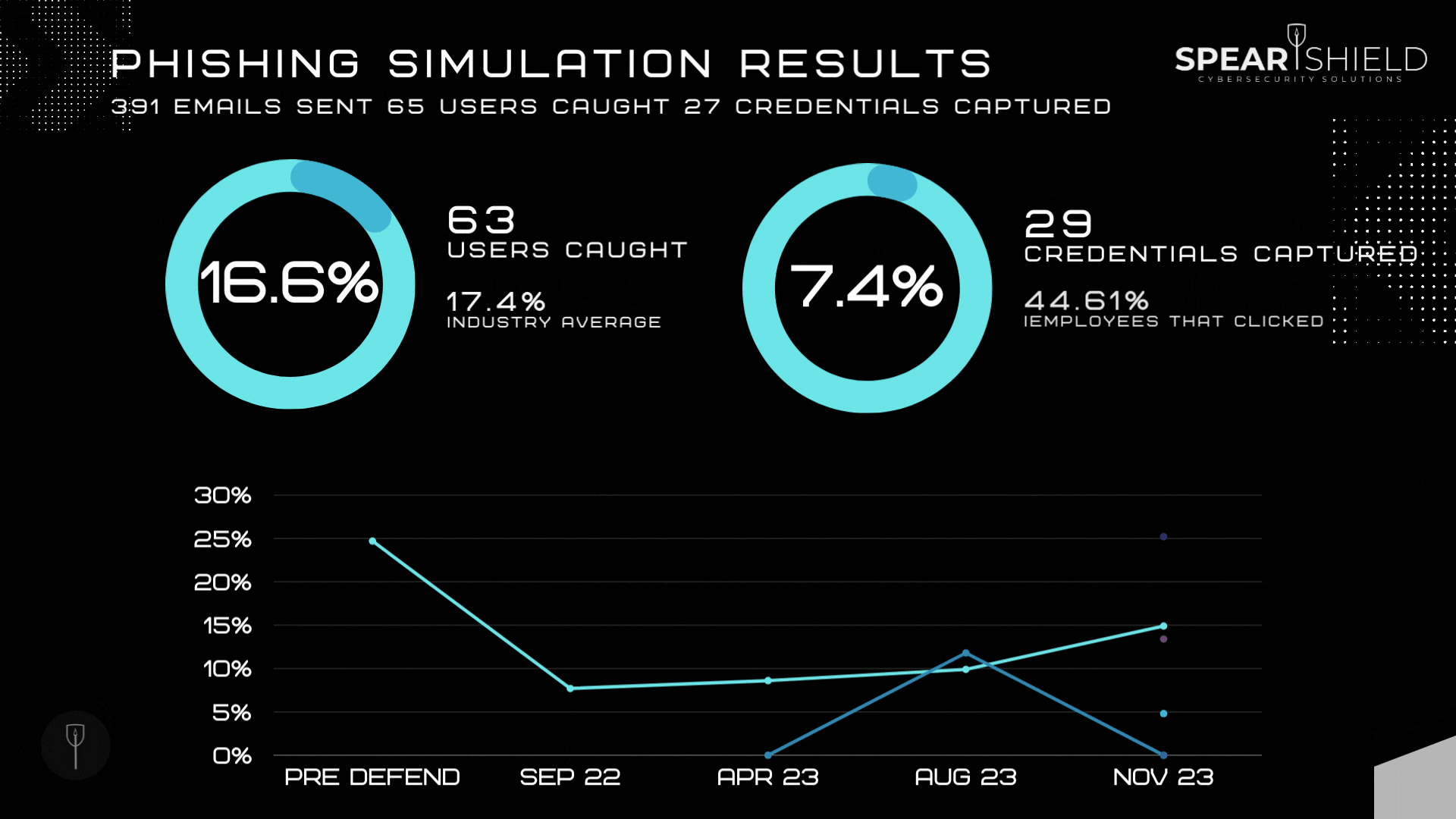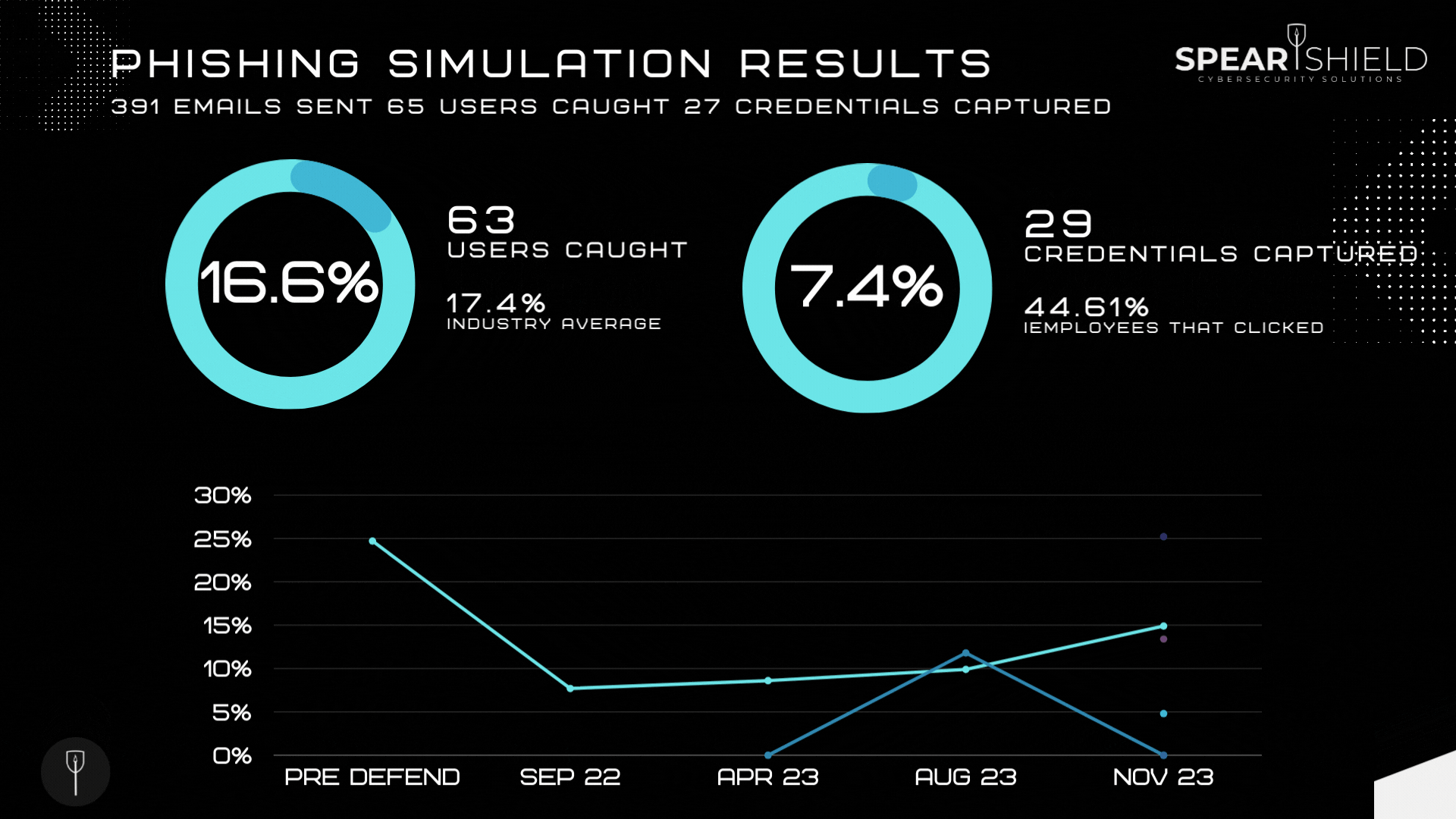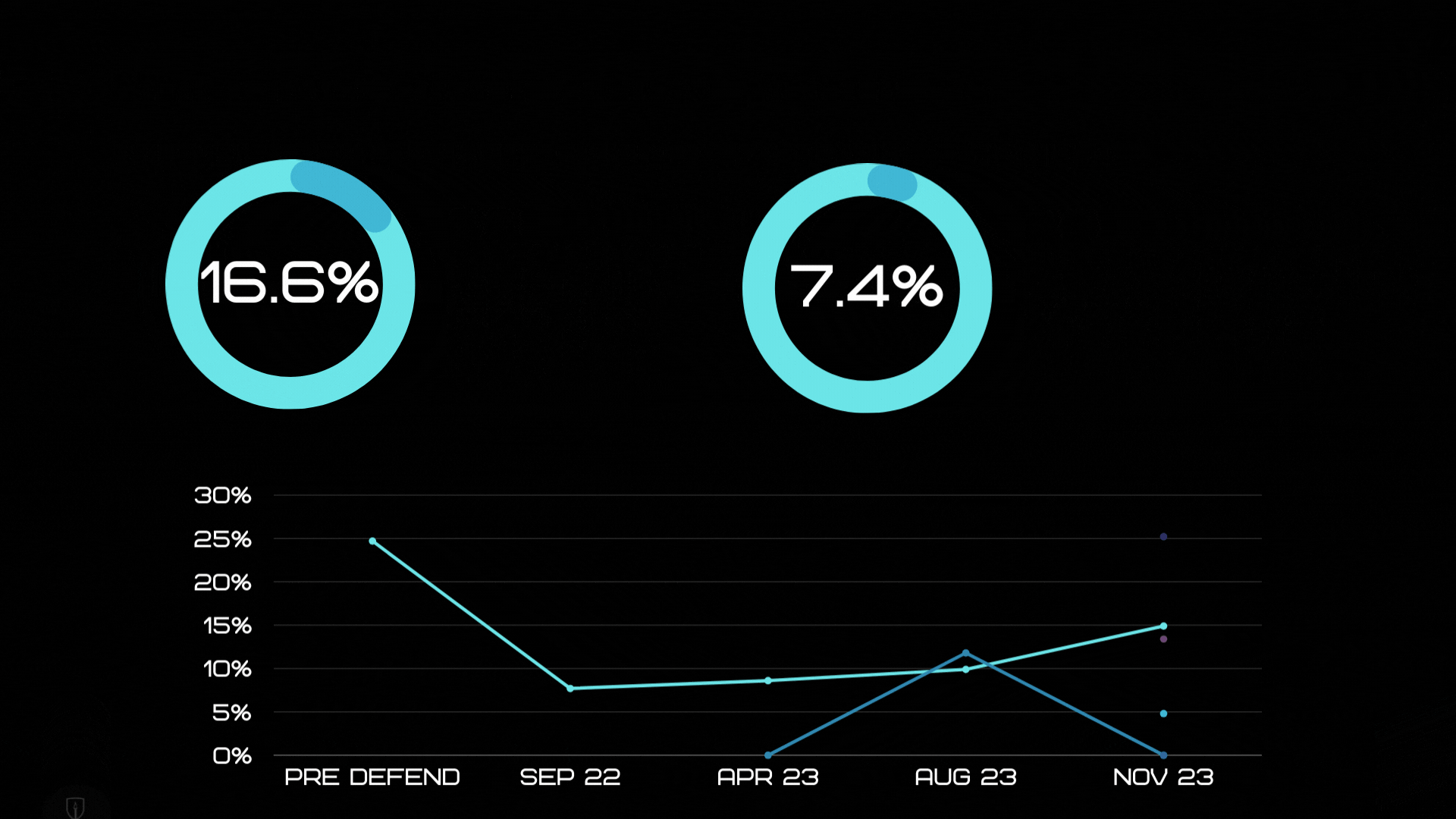
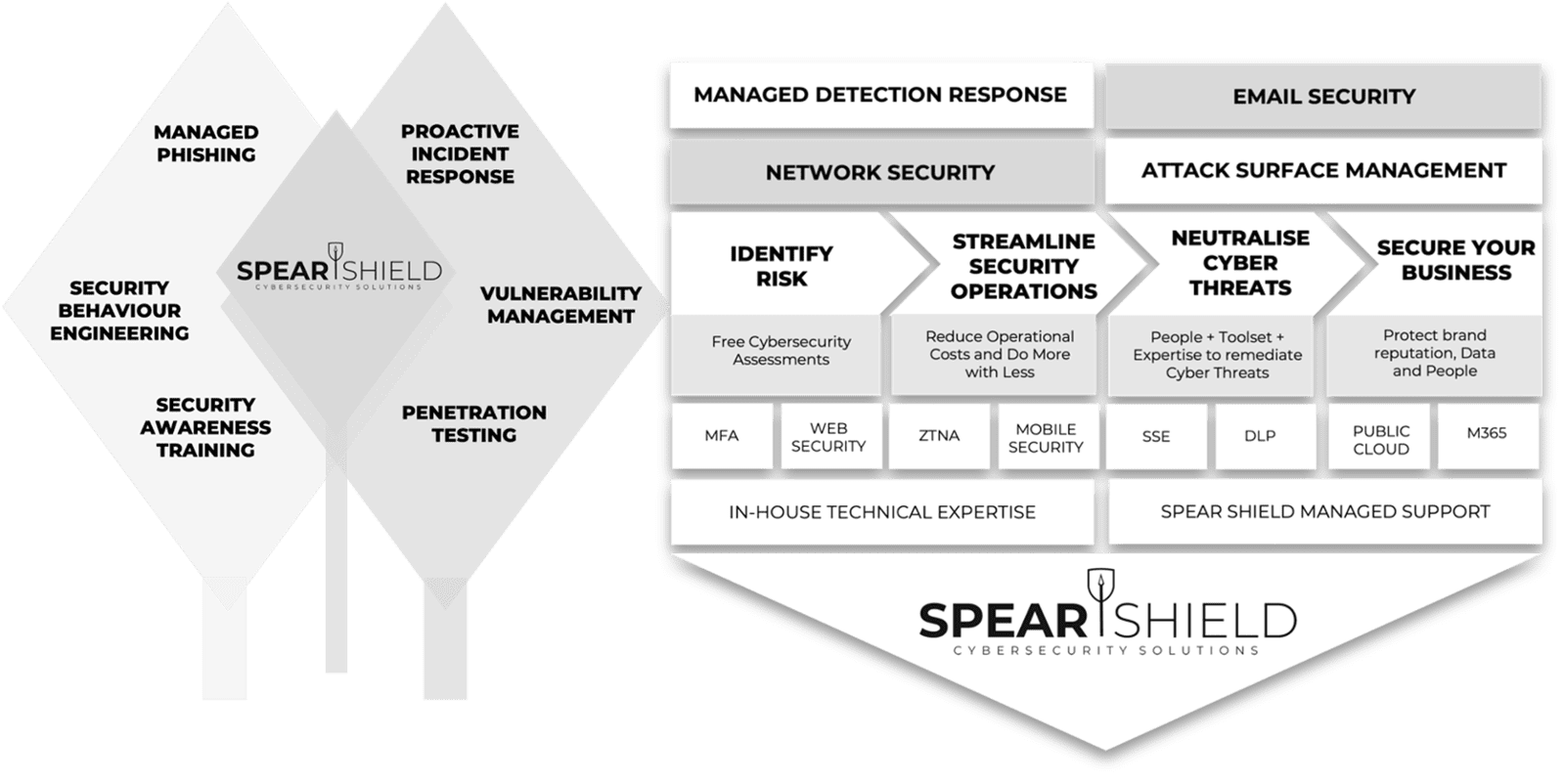
What are the benefits of running regular phishing campaigns?
How can I enhance user awareness and mitigate risk?
Achieving Security Outcomes Together
Mitigating Human-Activated Risk
Associate Director (Information and Security) Concertus, part of the Vertas Group.
Enhancing SecOps with 24/7 MDR
Head of I.T, Times Higher Education
IT Security validation with Penetration Testing
VIDEO COMING SOON
Achieving Supplier Assurance with Cyber Essentials Plus

'We're delighted with our data security efforts - we're Cyber Essentials Plus certified!
This wouldn't have been possible without the help of Spear Shield, trusted local cybersecurity experts here in Ipswich. As part of our commitment to safe recruiting, secure sensitive data is crucial. This certification proves our proactive measures to prevent cyber risks."
I.T Manager, Sanctuary Personnel
Understanding Human Risk with SAT
VIDEO COMING SOON
Why customers Secure with Spear Shield
FAQ's
Everything you need to know about Spear Shield.