Outcomes achieved with Automation
User Management use cases
Multiple factors of authentication are combined to provide robust security that is flexible for users but rigid against threat. The interface provides a fast, non-disruptive and simple authentication experience, helping users focus their time on what matters most.
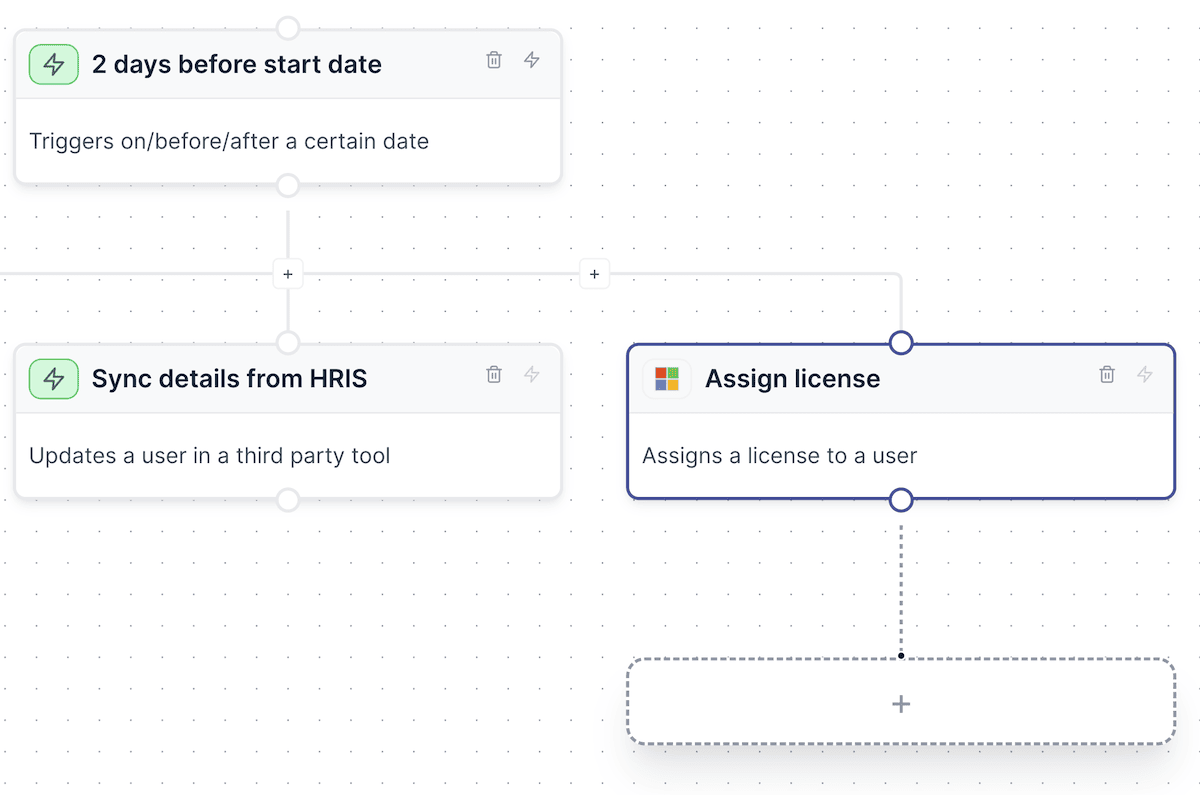
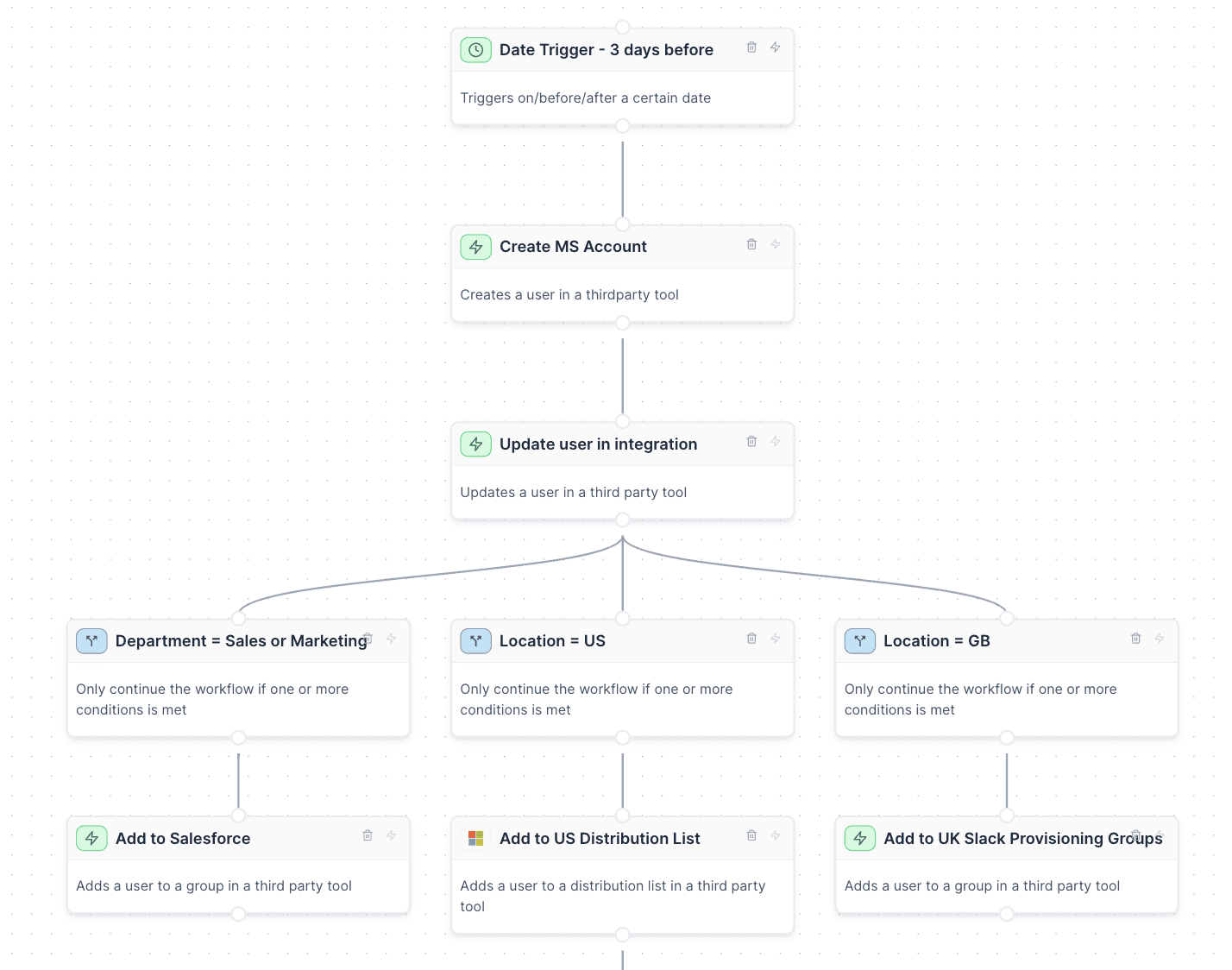
Automate onboarding
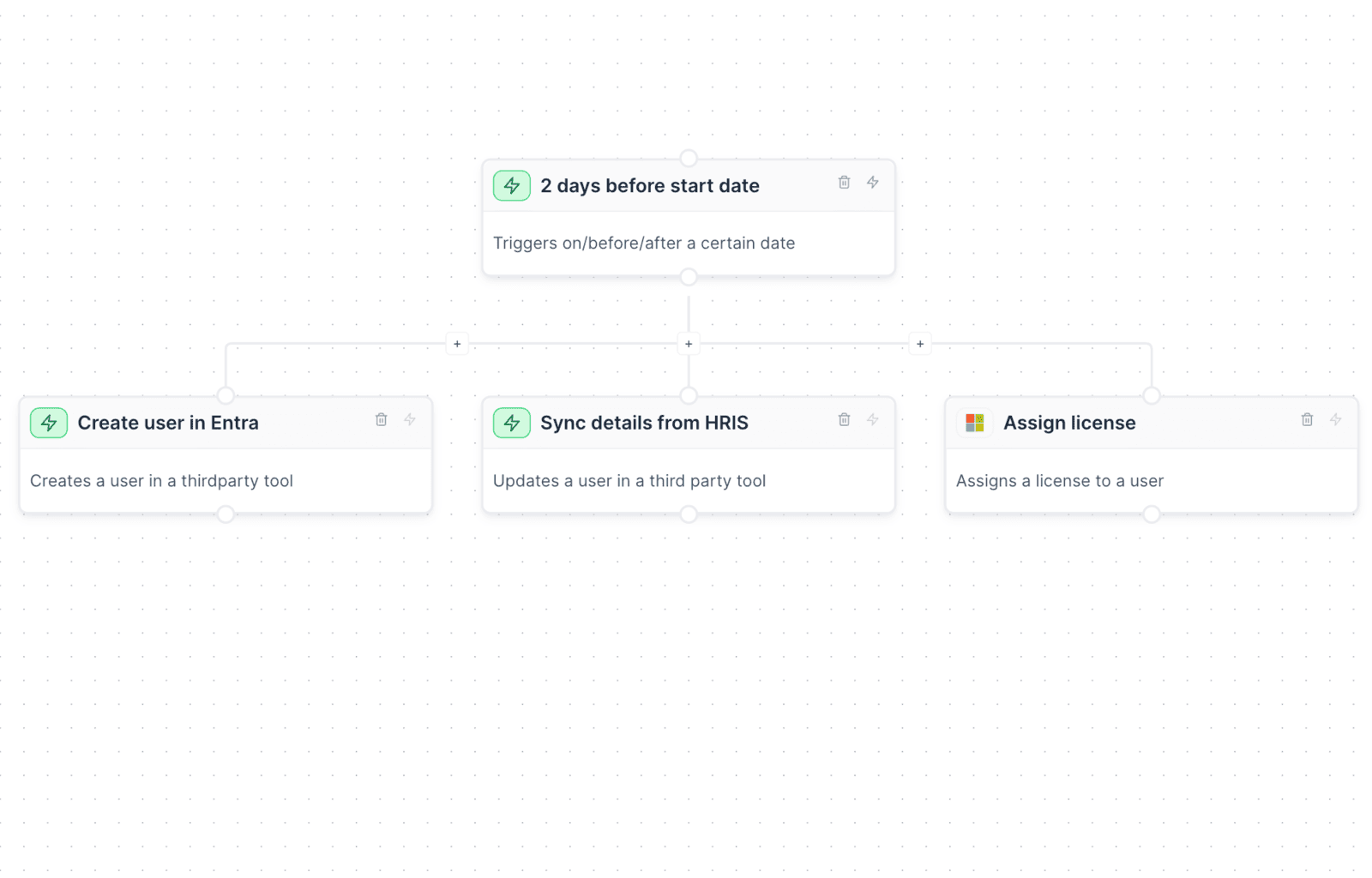
Simplify IT onboarding to a single click. Automatically create user profiles, manage distribution lists, and assign access packages seamlessly. Transform the way you onboard, ensuring a flawless start for every team member.
With integrations with your HRIS, you can trigger workflows based off your employee start dates, automatically create their accounts, create and assign licenses, allocate to groups and more.
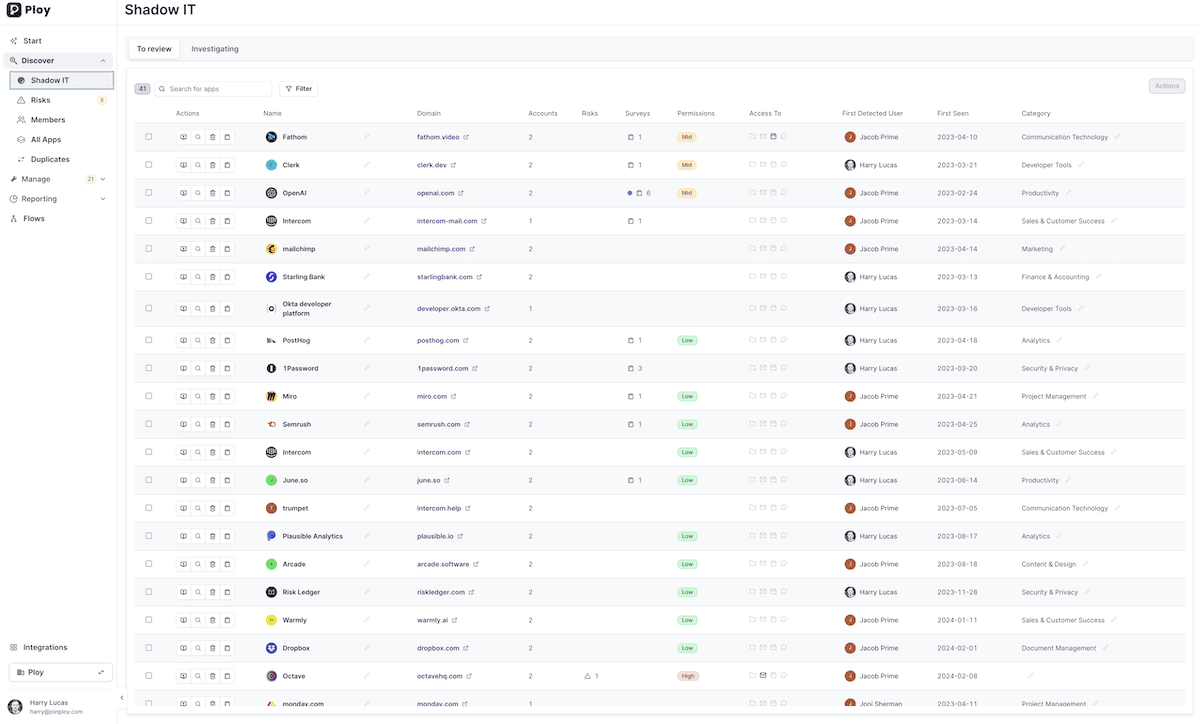
Shine a light on Shadow IT
Can't seem to get a handle on the applications employees are signing up for? Worse, what kinds of data they're sharing with those apps and permissions they're allowing? Ploy brings these apps into the light, giving you complete visibility and peace of mind of exactly what applications your employees are using.
Free SaaS Discovery Scan?
Achieving Security Outcomes Together
Mitigating Human-Activated Risk
Associate Director (Information and Security) Concertus, part of the Vertas Group.
Enhancing SecOps with 24/7 MDR
Head of I.T, Times Higher Education
IT Security validation with Penetration Testing
VIDEO COMING SOON
Achieving Supplier Assurance with Cyber Essentials Plus

'We're delighted with our data security efforts - we're Cyber Essentials Plus certified!
This wouldn't have been possible without the help of Spear Shield, trusted local cybersecurity experts here in Ipswich. As part of our commitment to safe recruiting, secure sensitive data is crucial. This certification proves our proactive measures to prevent cyber risks."
I.T Manager, Sanctuary Personnel
Understanding Human Risk with SAT
VIDEO COMING SOON
Why customers Secure with Spear Shield
FAQ's
Everything you need to know about Spear Shield.