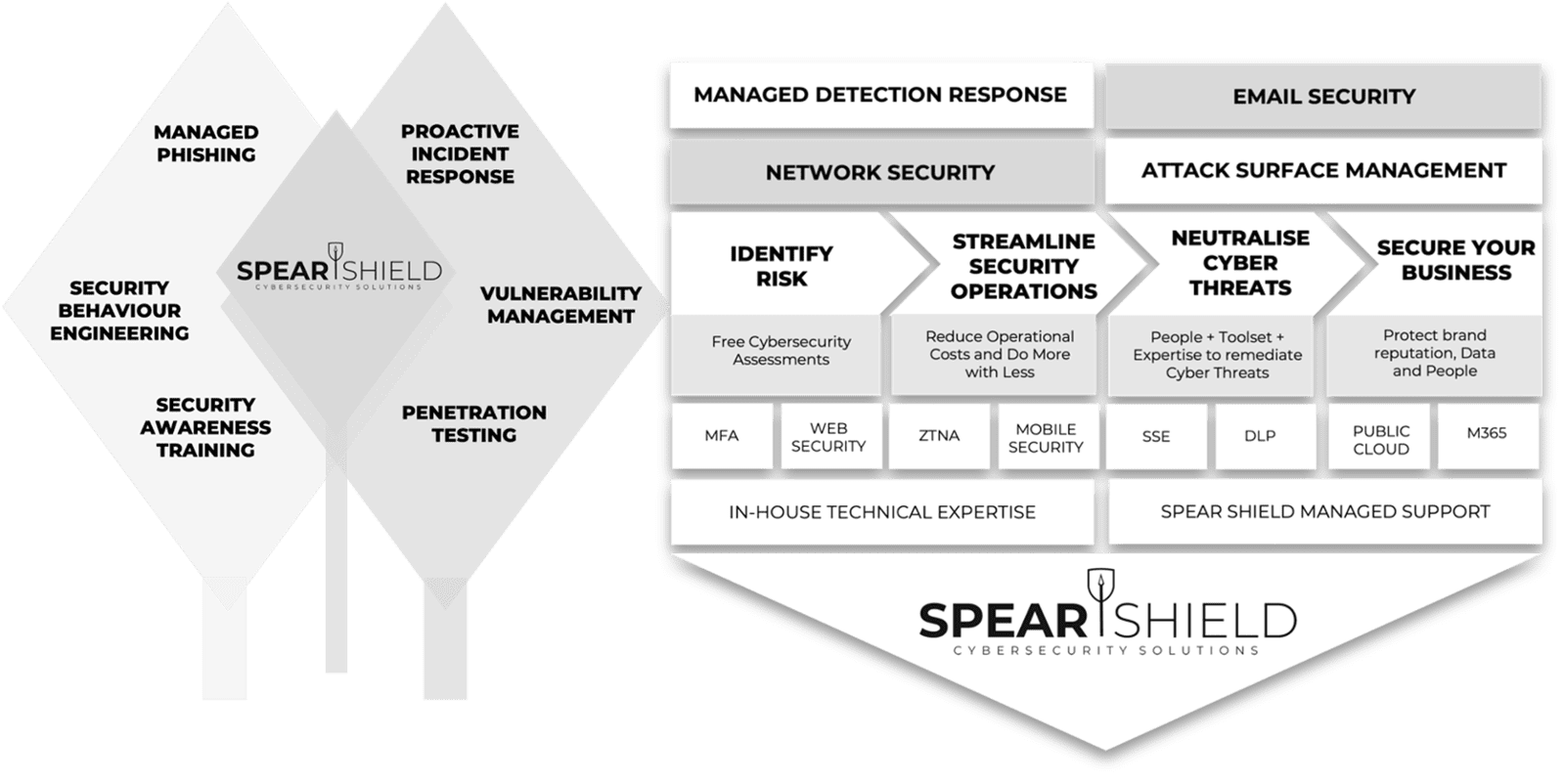
The 3 Stages of Data Security Everywhere
Cyber Security is Data Security
People are working anywhere with data everywhere, from any kind of device. Organisations are looking to accelerate business transformation, take advantage of new technologies like Generative AI and enable faster, safer and more seamless access to business data. The data problem is growing exponentially and there are more data risks to guard against than ever before. But here is where we can help...
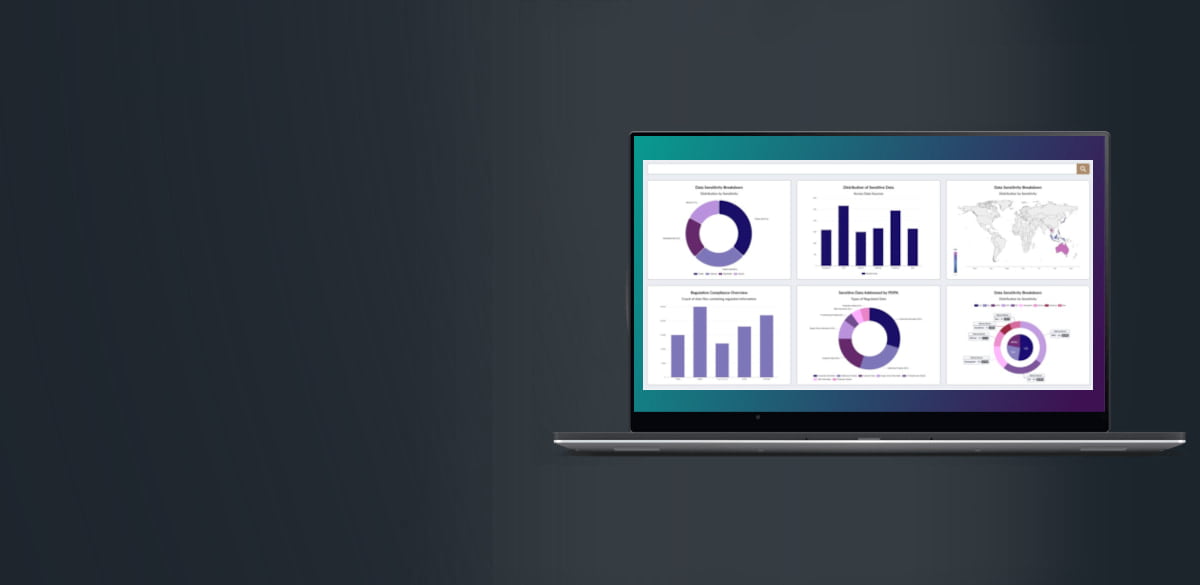
Step 1. Visibility - Data at Rest
Fast discovery of data using advanced AI and LLMs to deliver a highly accurate view of your unstructured data to provide you valuable insights by:
Continuous self-learning AI model for enhanced efficiency, personalisation, and accuracy.
Viewing who exactly has permission to your sensitive data to secure all data with least privilege access.
Reducing redundant, obsolete, and trivial data to simplify management and minimise loss of sensitive data.
Understanding risk for each file to maintain regulatory compliance more easily.
Providing location of your data by IP address and file paths.
Grouping data assets and cataloging to gain a bird’s-eye view into how best to organize your data.
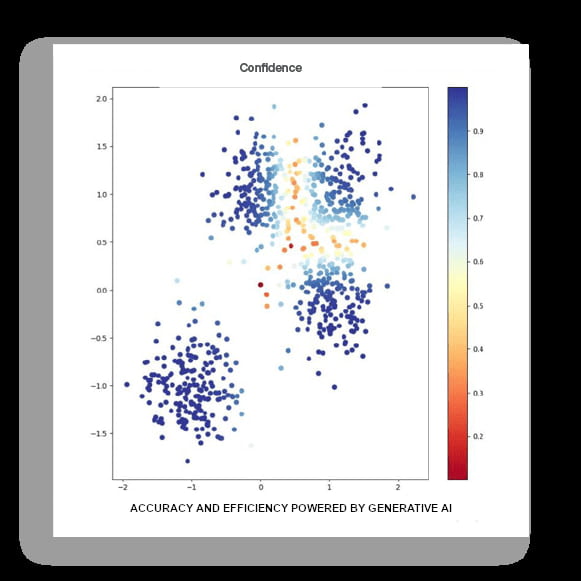
Step 2. Classification - Data Classification
Protecting data across cloud, endpoint, email, network, and web is an exhausting challenge. Spear Shield recommends Data Classification that leverages Artificial Intelligence (AI) and Large Language Models (LLMs) to increase the accuracy of data classification for unstructured data to improve your team’s efficiency, reduce false alerts, and better prevent data loss.
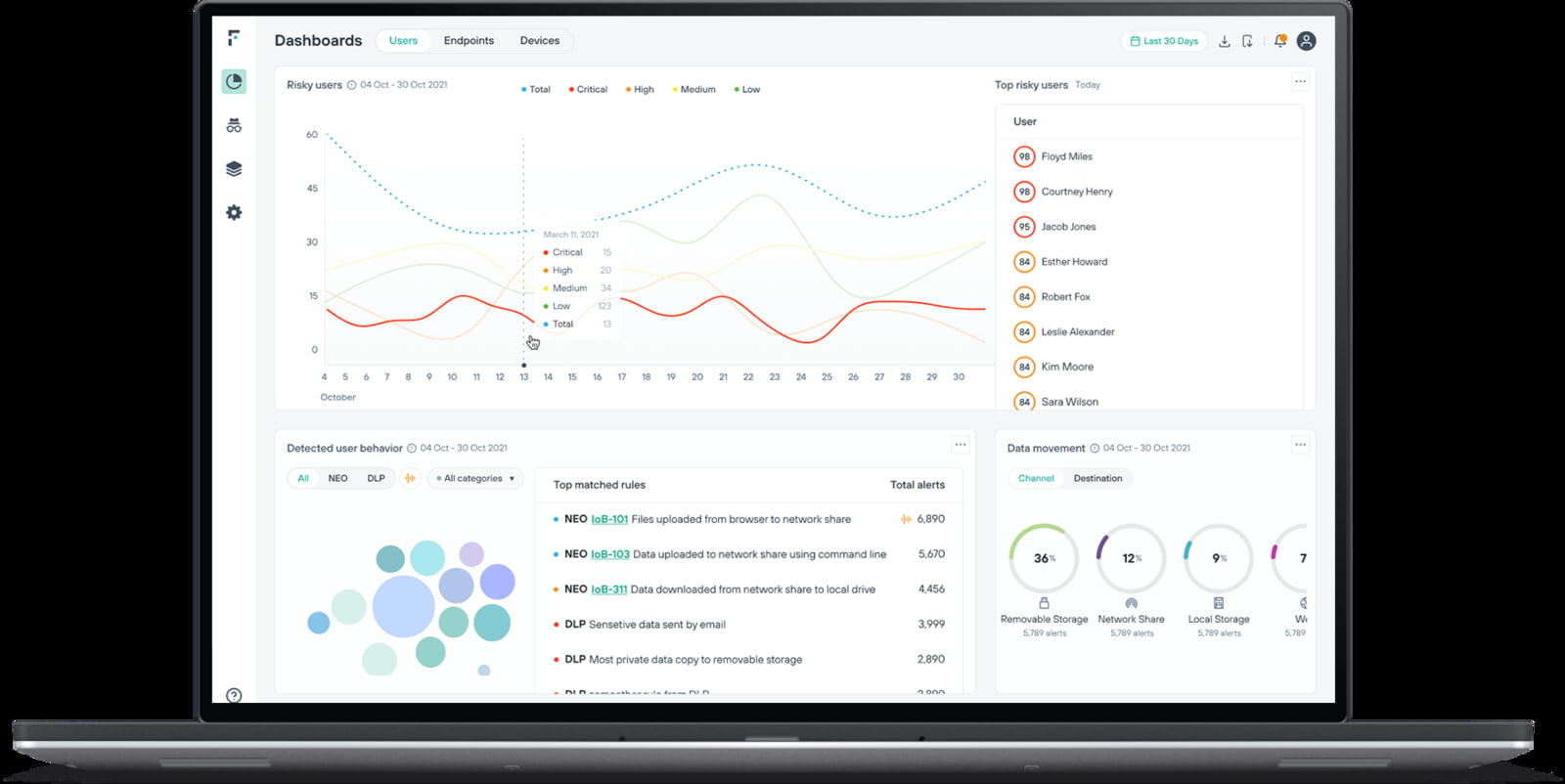
Step 3. Risk Adaptive DLP - Data In Motion
Taking a behaviour-centric approach to data security.
Gain better context and understanding of user intent by focusing on user behavior and their interaction with data
Increase employee productivity with individualised data security so low risk users can proceed as usual while limiting high risk user activity
Minimise false positives with a graduated approach to policy enforcement based on risk level so practitioners don’t experience alert overload
Enable safe collaboration on cloud applications by gaining insights to user engagement with cloud data
Investigate risk from insiders with efficiency and ease
Free Data Risk Assessment?
Achieving Security Outcomes Together
Mitigating Human-Activated Risk
Associate Director (Information and Security) Concertus, part of the Vertas Group.
Enhancing SecOps with 24/7 MDR
Head of I.T, Times Higher Education
IT Security validation with Penetration Testing
VIDEO COMING SOON
Achieving Supplier Assurance with Cyber Essentials Plus

'We're delighted with our data security efforts - we're Cyber Essentials Plus certified!
This wouldn't have been possible without the help of Spear Shield, trusted local cybersecurity experts here in Ipswich. As part of our commitment to safe recruiting, secure sensitive data is crucial. This certification proves our proactive measures to prevent cyber risks."
I.T Manager, Sanctuary Personnel
Understanding Human Risk with SAT
VIDEO COMING SOON
Why customers Secure with Spear Shield
FAQ's
Everything you need to know about Spear Shield.