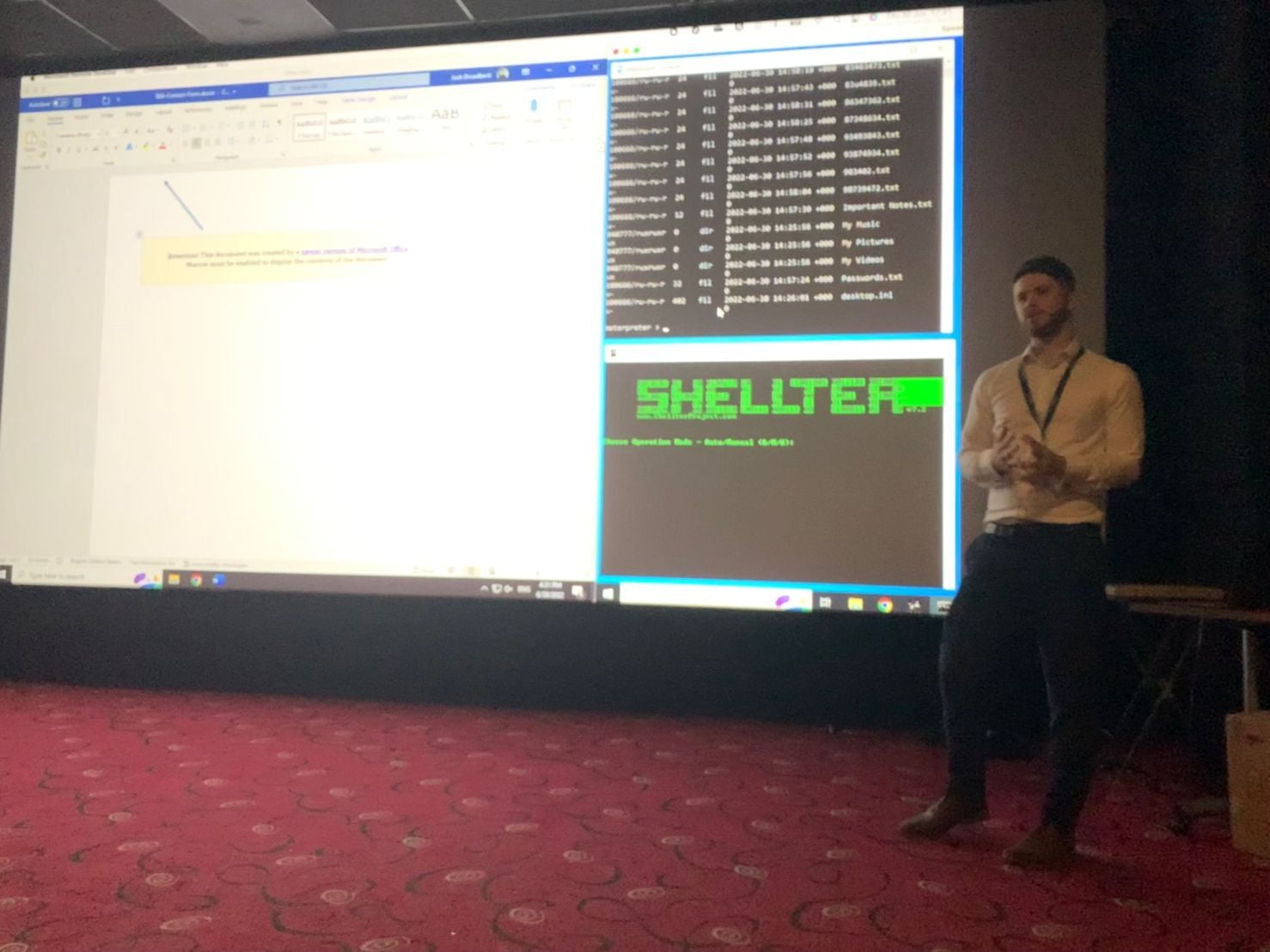
The team at Spear Shield has reeled in the phishing net and analysed the data of over 30k+ phishing emails sent to users across over 20+ different organisations from our Managed Phishing Simulation service findings over the past year. This blog post has been designed to share insights and practical guidance from our own experience on how to conduct a successful internal phishing simulation and user awareness campaign.
The Highlights
Introduction
Importance of Phishing for enhancing awareness
Phishing simulations are a crucial exercise for increasing cyber security awareness and enhancing that knowledge within organisations. It's important to empower users to recognise and effectively take action against phishing threats of varying type and payloads.
Why is phishing such a popular attack vector? Hacking a human is often easier than hacking software as it exploits the natural human tendencies of trust and curiosity, which can bypass even the most sophisticated technical security measures.
Managed Phishing Overview
What is Managed Phishing and why is it important for organisations?
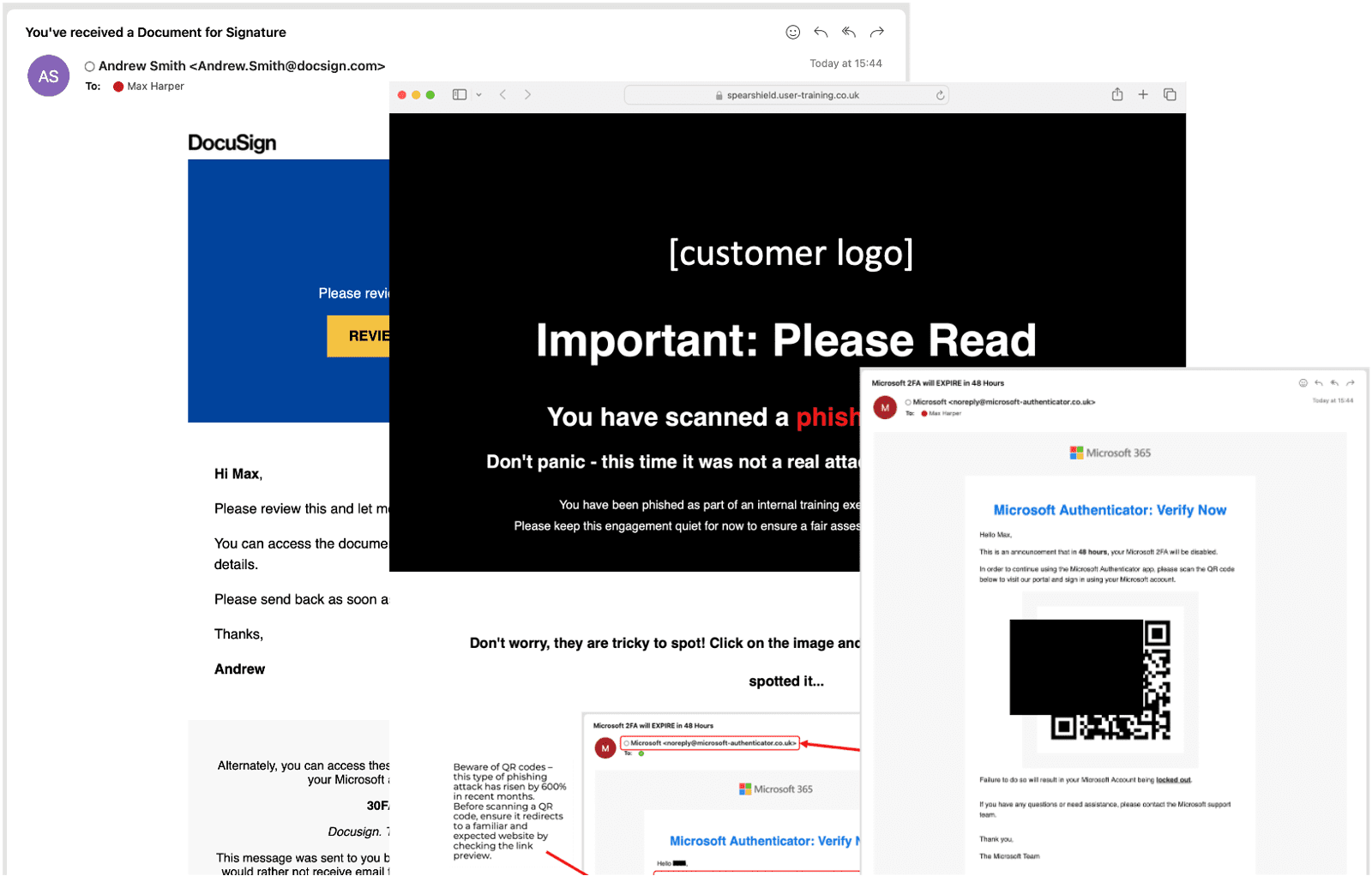
- Spear Shield's managed phishing service is a great way to understand the level of human-activated risk you have within your organisation. This is conducted through a fully customisable phishing simulation and can include a variety of payloads such as links, QR codes or attachments. Users can be redirected to legitimate web pages (normally for baseline simulations), credential harvesting pages or related training content. Spear Shield have access to a vast amount of email threat intelligence data, allowing phishing simulations to be created and carried out in relation to the most prevalent threats.
The importance of running regular campaigns
- Regular phishing simulations are essential as they keep employees alert and proficient in identifying evolving email threats. The simulations can also highlight: repeat offenders that might need some extra targeted training, an area of weakness that might require additional wider cyber security training and/or the need for an additional layer of protection. Regular simulations can also provide insight into reporting culture and allow for those processes to be streamlined.
Spear Shield's Phishing Methodology
Methodology for choosing different campaigns for different customers
- Choose payload (link, attachment, QR code)
- Choose email template & landing pages (credential harvest, training, etc.)
- Whitelist IP addresses & domains (full steps provided)
- Test deliverability and tracking
- Schedule emails (drip feed approach or 'big bang' style)
- Capture results - it's always recommended to allow a small period of time to account for users that might be on leave.
- Present results & recommendations
Different phishing campaign types and customer specific scenarios
- Baseline simulations - these typically include a fairly generic template such as a Microsoft OneDrive file share to allow organisations to understand their base level of cyber security awareness when it comes to phishing. The links normally redirect to a legitimate looking landing page to keep suspicions low and ensure a fair test for all users.
- Credential Harvesting – Often the main goal of an attacker is to capture a user’s username and password. These days hackers don’t break in, they log in. A credential harvesting simulation evaluates an organisation’s user’s susceptibility to entering their credentials on a fake web page. Spear Shield can offer a wide range of credential harvesting scenarios but always recommend relating this to an internally used system to keep this as authentic a test as possible.
- Spear Shield Cyber Academy – an LMS style platform that allows users to undergo a baseline assessment to understand their level of understanding. After that, a fully customised 12 month training program will be created for each user based on their results.
- Attachment – More and more attackers are using attachments to evade security layers. Attachments are often abused as part of supply chain compromise attacks and will contain links to legitimate compromised domains. For example, it might be a link to a Word document hosted in SharePoint. Within that document is a malicious link that takes the user to a credential harvest. Spear Shield have the capability to track a number of attachments and that includes opens, clicks and even redirecting to credential harvests.
- Spear Phishing – highly targeted and personalised attacks like spear phish are very important to simulate. These attacks often produce much higher click rates due to the fact that they often appear far more authentic and trustworthy when compared to a generic phish. The email may ‘appear’ to come from a trusted user or discuss certain familiar topics.
Key Findings
| Customers without Egress Defend | Customers with Egress Defend | |
| Overall Click Rate: | 35.7% | 7.3% |
| Overall Cred Rate: | 16.0% | 6.4% |
| Microsoft: | 28.5% | 5.8% |
| Brand Impersonation: | 48% | 7.8% |
| Spear Phish Impersonation: | 47.7% | 22.5% |
| Google: | 38.8% | 0% |
| Apple: | 9.1% | - |

Spear Shield Customer Success Stories
By providing employees with a technological safeguard that is designed to provide real-time teachable moments at the point of risk (click here to learn more), our customer's have been able to able to achieve dramatic reductions in their phishing simulation click-rates without having to impact productivity and take employee's away from their day jobs to perform online or classroom based training.
Private Healthcare - 300 users = 75% click-rate reduced to 1.6%
Recruitment - 500 users = 24.7% click-rate reduced to 7.7%
Construction - 100 users = 40.7% click-rate reduced to 0%
Financial Services - 150 users = 82.5% click-rate reduced to 1.3%
Hospitality - 4,500 users = 35.1% click-rate reduced to 3.8%
Pharmaceutical - 2,000 users = 16.3% click-rate reduced to 0.5%
Recommendations for running a successful Phishing Campaign (the do's and don'ts!)
Do:
- Tailor phishing simulations to real-world attacks and don't 'go easy'. The bad guys will not be going easy on the organisation they target.
- Use a range of payloads and themes to understand what users are most susceptible to and then tailor internal comms and training to educate them between simulations.
- Provide feedback - Spear Shield provide a campaign summary poster that can be sent round or uploaded to internal systems such as intranets.
- Always tell who you're impersonating, you're impersonating them
- Internal recognition and praise for users performing well and reporting
- Make simulations predictable - avoid running simulations on a predictable schedule.
- Penalise users for negative interactions with phishing simulations. The goal is to educate and create a positive cyber security culture.
- Neglect to analyst the results - bypassing the step of reviewing outcomes post-simulation misses a valuable chance to understand and enhance awareness about the level of risk, both at an individual and organisational levell.
- Use overly sensitive content - things like pay, bonuses or anything sensitive that could upset an employee.
What to expect for the future of phishing attacks in 2024
Attack types continuing to increase in complexity
More sophisticated threats are on the rise and we continue into 2024 with a huge increase in QR code Phish. They're being used in both the body of the email and within attached documents. This method takes advantage of the ease and convenience with which QR codes are used, often bypassing traditional email threat protection.
SMTP smuggling attacks exploit vulnerabilities in SMTP servers. These sophisticated attacks involve inserting malicious commands into email headers to bypass security filters, allowing attackers to smuggle harmful content through to end user inboxes undetected.
Both methods signify a shift towards more innovate and covert techniques in the cyber threat landscape, emphasising the need for updated and more comprehensive security measures such as an Integrated Cloud Email Security (ICES) layer.
How Spear Shield can help if you're reviewing User Awareness and Training in 2024
- Managed Phishing Simulation Service (click here to learn more)
- Spear Shield Cyber Academy (click here to learn more)
- Real-Time User Awareness and Education (click here to learn more)
FREE Email Security Assessment
- How many dangerous emails are slipping through the net
- How susceptible users are to phishing attacks
- An understanding of the effectiveness of real-time teachable moments to help change users security behaviours at the point of risk
- 30 Minute remote session for set-up
- 15 Minute remote session for half way catch-up
- 30 Minute remote session to present findings