
Why are brand impersonation attacks so effective?
Everyone loves a discount! Particularly during a cost of living crisis, this makes people more likely to click on the fraudulent offers they receive via email.
Let's take a look at a trending example...

Shein is reported to be the largest online-only fashion retailer in the world, with a valuation of $100bn. As a result, it's a highly popular household name with a significant audience. Like every retail brand, customers are going to be no stranger to receiving regular marketing emails, designed to engage customers and increase sales.
This particular phishing attack includes use of a look-a-like email domain and websites, with the aim of stealing people's log-in credentials and payment details, and taking fraudulent payments.
Spear Shield partner's Egress, Threat Intelligence team has detected a 128% increase in Shein brand impersonation emails since 1st January 2023, compared with November 2022.
How is the phish constructed?
Sent from a spoofed domain that impersonates Shein, such as 'shien', instead of 'shein'. Also, sent from unclaimed domains such as shein.ru.
Despite the use of spoofed domains, the emails passed DMARC authentication. They were also sent via legitimate third-party mailing platforms (such as Salesforce and Mailchimp).
The email design itself, is an exact replica of a Marketing email that Deal Town, an online archive of email newsletters, records as being sent on 17th June 2022. It's likely the cyber criminals used the existing email as their template when creating the attack to add credibility, but even included the incorrect spelling and grammar you can see in the image 'Have we meet?'.
"There's a phish for everyone..."
Microsoft was the second most impersonated brand in 2022, representing 13% of all phishing pages according to csoonline.
As more and more organisations continue to adopt Microsoft 365, users are new to to some of the emails they're receiving, and could be lured into a false sense of security...

Netflix and Adobe, were other highly-impersonated brands but Facebook takes the claim as the number 1 impersonated brand in 2022.
Detecting brand impersonation attacks
As you can see in these examples, it can be incredibly difficult for the average user to detect sophisticated impersonation attacks. If there's any doubt about the legitimacy of an email where there's e.g a promo code, it's possible to navigate to the real website via your browse or search engine and enter the code there.
Techniques used to increase deliverability
Cyber criminals use a combination of techniques to improve deliverability, making it more likely that these kind of emails will be sent to your user's inbox, rather than quarantined by a SEG or sent to the Junk folder by Microsoft.
Even though most are using lookalike domains, if an email passes DMARC authentication, it makes it much more difficult for signature-based anti-phishing technologies (like secure email gateways (SEGs) to be able to detect them.
Finally, the use of legitimate mailing platforms (e.g Salesforce and Mailchimp) to send these attacks increases their deliverability rate, making it less likely they'll be filtered out by spam filters or signature-based detection.
How can i mitigate risk of phishing and help support my users?
Our recommendation here at Spear Shield is combining security awareness and training with real-time teachable moments at the point of risk.
Transformative and engaging training content has its place, but it's an activity, not an outcome. This needs to be combined with interventions or nudges when they're most needed - when people are carrying out risky actions in real-time.
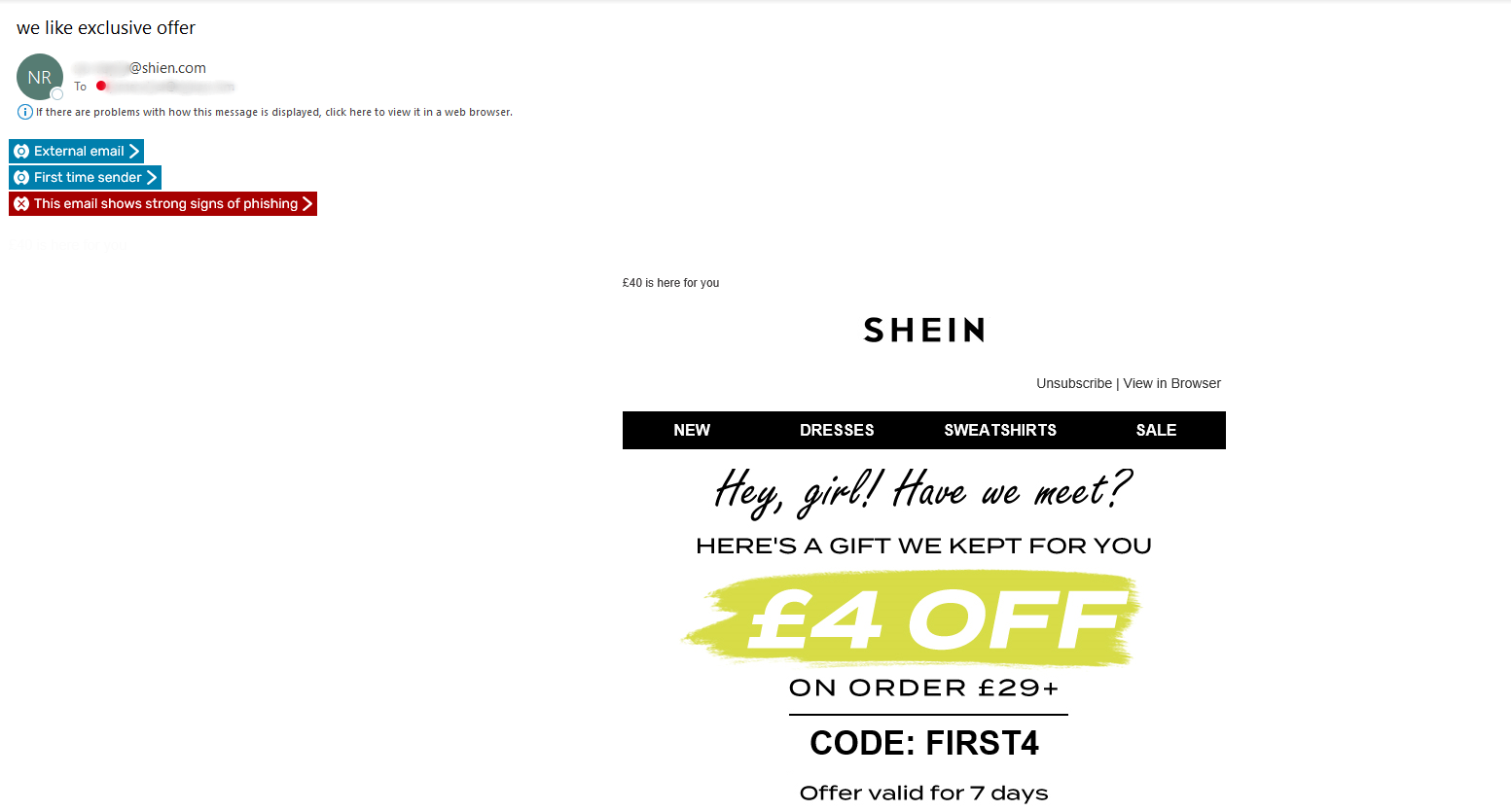
You may have noticed the dynamic HTML banners injected into into each of the emails in the screenshots - 'This email shows strong signs of phishing' these are what we refer to as 'real-time teachable moments'.
✔️ Intelligent, dynamic DLP prompt to alert the user that they're about to respond to a dangerous email or a warning message if they're about to send the wrong address, attach an incorrect file, or use an inappropriate level of encryption.
These teachable moments are designed to not only stop breaches in the moment, but also to educate your users in real-time as to why an action has been flagged, reinforcing Security Awareness & Training, and boosting the ROI of training efforts.
With the combined approach, our customers benefit from being able to genuinely understand their risk on a per person basis, rather than at an organisational level only.
Interested to learn how Spear Shield and their customers are able to detect and respond to sophisticated phishing attacks like brand impersonation attempts that are able to slip through the net?
Spear Shield are currently running a FREE Email security assessment that can help you identify:
- Total number of Dangerous and Suspicious emails detected landing into employees inboxes throughout the engagement
- Insight into the top types of phishing emails your organisation is receiving
- Insight into the top types of payloads being used in the phishing emails your organisation is receiving
- Insight into your Supply Chain Health (DMARC status of inbound emails)
- Insight if there are live phishing attacks sat in employees inboxes that can be remediated together
- Phishing Simulation results (with and without an ICES solution implemented)
- Previous caught user analysis breakdown
- Insight into how many users were stopped in their tracks at the link advisory page
- Insight into the reporting heroes in your organisation
- Insight into what device type your employees are engaging business emails on. (mobile, PC, both)
- Consultative recommendations for security best practice
If you'd like to learn more, you can visit https://www.spearshield.co.uk/human-activated-risk or contact the team today:
01473 948980
About Spear Shield
Here at Spear Shield, we are continuing to invest in our goal to create one of the most cyber-secure client communities in Suffolk, East Anglia and across the UK.



